Data Center Physical Security Best Practices
Published on May 23, 2023,
by
In an era of rising cyber and physical threats, securing your infrastructure goes beyond firewalls and encryption. Data center physical security is a foundational layer of protection—guarding against unauthorized access, tampering, and downtime. From perimeter defenses and biometric access to surveillance and secure media handling, implementing best practices ensures operational continuity and regulatory compliance
Layered Security
Layered security, also known as defense in depth, is a critical component of data center physical security. This strategy doesn't rely on a single defense mechanism but deploys multiple layers of security measures to protect the data center from various threats. The logic behind this approach is that even if one layer is compromised, subsequent layers continue to provide protection, thereby increasing the overall security.

The concept of layered security is reminiscent of the fortification approach adopted in medieval castle designs. Castles were designed with multiple layers of defense, each acting as a deterrent and a line of resistance against invading forces. Below, we illustrate how the principles of medieval castle fortifications can be applied to data center security.
- Outer Wall and Moat: The outer wall of a castle with a moat was the first line of defense, deterring casual intruders and slowing down more determined attackers. In a data center, this is equivalent to perimeter fencing, external surveillance cameras, and alarm systems. These measures discourage unauthorized individuals from attempting to breach the premises.
- Drawbridge and Gatehouse: The drawbridge served as a controlled entrance and exit point, while the gatehouse housed guards and offered additional fortification. In a data center, this refers to secure entry points managed by security personnel. Access control systems, such as biometric scans or card readers, are essential here.
- Bailey: This open space within the castle walls allowed defenders to spot and respond to any intruders who had breached the outer wall. Similarly, internal surveillance cameras and motion detectors within a data center can alert security personnel to any unauthorized persons who have made it past the initial layers of defense.
- Keep: The keep was the last line of defense and the most heavily fortified part of the castle, housing the lord and his valuables. Similarly, the server rooms in a data center are akin to the keep. These areas should be the most secure, with additional access control measures in place, like mantraps, and under constant surveillance.
- Multiple Entrances and Exits: Castles often had secret passages and multiple entrances/exits, used for surprise attacks or emergency escapes. Similarly, having clearly marked emergency exits in a data center is vital for evacuations during emergencies while maintaining security protocols to avoid these becoming a security loophole.
Just as medieval castles were not impregnable, modern data centers cannot claim to be absolutely secure. However, the layered security approach minimizes risks and ensures a robust defense mechanism against potential physical security threats. By learning from history and adopting a layered security strategy, data centers can strengthen their security posture and safeguard the precious data they house.
Secure Access Control
Secure access control is a fundamental element of data center physical security, ensuring that only authorized individuals have access to sensitive areas. The purpose of these systems is to provide a robust and manageable method for authenticating individuals before granting them access to the facility or specific parts within it. This procedure minimizes the risk of unauthorized access and potential physical threats to the infrastructure and data.

One of the most widely implemented forms of secure access control in data centers is the badge reader system. This method uses a physical badge, often in the form of a card, that carries a unique identification number for each employee or visitor. This badge is scanned by a badge reader at various checkpoints, verifying the identity of the individual and granting them access based on pre-set permissions.
Here are some ways in which badge reader systems enhance data center security:
- Authentication: Badge reader systems authenticate individuals based on the unique identifier present on their badges. Only those with valid badges can gain access, providing a reliable means to verify the identity of each individual entering the data center.
- Authorization: Badge reader systems can be programmed to provide different levels of access to different individuals. This granularity is crucial in data centers where different employees have varied responsibilities. For instance, an IT manager may have access to server rooms, while a non-IT employee may be restricted to common areas.
- Audit Trails: These systems create an audit trail of entries and exits, recording who accessed which areas of the data center and at what times. This information can be critical in investigations following a security incident.
- Integration with Other Systems: Badge reader systems can often be integrated with other security systems such as video surveillance or intrusion detection systems. When an individual uses their badge to access a particular area, the surveillance camera can be prompted to record the event, providing visual verification of the individual's identity.
- Lost or Stolen Badges: If a badge is lost or stolen, it can be immediately deactivated in the system, preventing misuse. A new badge with a different unique identifier can then be issued to the employee.
While badge reader systems provide significant security benefits, they must be part of a comprehensive access control strategy. Supplementing them with other technologies such as biometric systems (like fingerprint or retina scanners) and pin code systems can add an extra layer of security. Multi-factor authentication, which requires two or more methods of verification, further strengthens access control, making it harder for unauthorized individuals to gain access.
In summary, badge reader systems play a vital role in secure access control, helping protect data centers from physical threats. However, their effectiveness depends on regular updates, diligent management, and their integration within a broader, layered security approach.
Surveillance Systems
Surveillance systems play a crucial role in the physical security strategy of data centers. They act as the eyes of the data center, providing real-time monitoring and recording activities to detect, deter, and document security incidents. Here's a closer look at how these systems enhance the physical security of data centers.

- CCTV Cameras: Closed-Circuit Television (CCTV) cameras form the backbone of most surveillance systems. These cameras should be strategically placed to cover all areas of the data center - both inside and outside. Critical areas like the server room, entrances and exits, and perimeter boundaries require special attention. Modern CCTV cameras offer high-resolution video, night vision, and motion detection capabilities. They may also come in two variants: fixed and pan-tilt-zoom (PTZ). While fixed cameras cover a particular field of view, PTZ cameras can be remotely controlled to monitor a larger area.
- Intrusion Detection Systems: These systems consist of sensors installed at various points of the facility to detect unauthorized access or suspicious activities. Types of sensors used can include motion sensors, glass break detectors, door contact sensors, and vibration sensors. When the system detects an intrusion, it sends alerts to security personnel or the security control center.
- Video Analytics: This is an advanced technology that uses artificial intelligence (AI) and machine learning algorithms to analyze video footage from CCTV cameras. It can recognize patterns, detect anomalies, and alert security personnel to potential threats. For instance, it can identify if a person is loitering in a sensitive area or if an object has been left unattended.
- Access Control Integration: Surveillance systems can be integrated with access control systems for enhanced security. When an individual uses their access credentials (like a badge or biometric data), the corresponding CCTV camera can document the event. This provides visual verification of the person's identity and creates a more comprehensive security record.
- Data Storage and Management: Surveillance systems generate vast amounts of data, which need to be properly stored and managed. The data should be securely stored for a period of time dictated by company policy or relevant regulations. Regular audits of this data can provide valuable insights into the efficiency of the security system and help identify potential vulnerabilities.
- Regular Maintenance: Like any other system, surveillance systems require regular maintenance to function optimally. This includes cleaning camera lenses, checking the field of view, ensuring proper functioning of sensors, and testing the system's overall performance.
Implementing an effective surveillance system in a data center involves more than just installing cameras and sensors. It requires careful planning to identify critical areas, choosing the right equipment, and integrating it with other security systems. Regular audits and upgrades are also necessary to ensure the system continues to provide robust security in an ever-evolving threat landscape.
Fire Suppression Systems
Fire suppression systems are an essential component of a data center's physical security strategy. The concentration of electronic equipment, power systems, and cabling within a data center significantly increases the risk of fire, making fire detection and suppression systems indispensable.
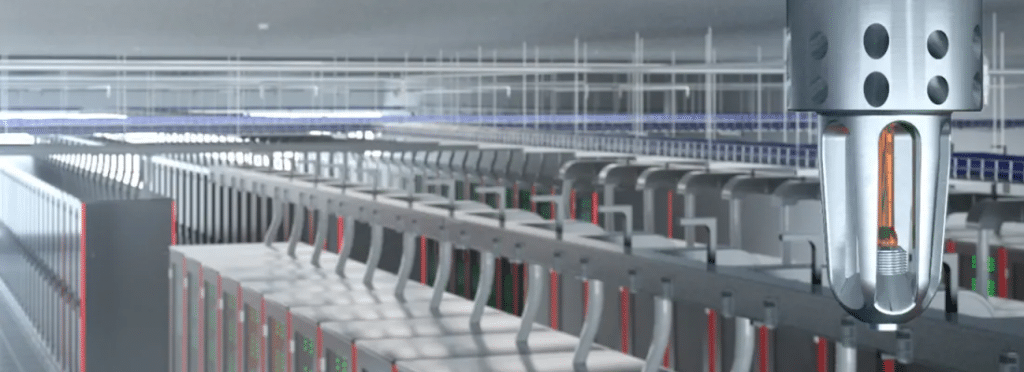
A comprehensive fire suppression system consists of several key components:
- Fire Detection Systems: These systems include smoke detectors, heat detectors, and air sampling systems. Smoke detectors and heat detectors identify smoke and unusual heat increases, respectively, while air sampling systems constantly monitor the air for particles associated with combustion. These detection systems should be installed throughout the data center, with particular focus on high-risk areas like server rooms and power supply rooms.
- Fire Alarm Systems: When the fire detection system identifies a potential fire, it activates the fire alarm system. The alarm system not only alerts personnel within the data center, but also sends a signal to a central monitoring service or the local fire department.
- Fire Suppression Systems: Once a potential fire is detected, the fire suppression system is triggered. There are several types of suppression systems suitable for data centers:
- Gas-Based Systems: These systems release fire-suppressing gases like FM-200 or Inergen, which work by reducing the oxygen level in the room or by absorbing heat. These gases leave no residue, minimizing damage to sensitive equipment.
- Water-Based Systems: Traditional sprinkler systems are less common in data centers due to the potential for water damage to equipment. However, newer technologies such as high-pressure mist systems can provide effective fire suppression with minimal water usage, reducing potential damage.
- Chemical Aerosol Systems: These systems use a fire-suppressing aerosol mist to extinguish fires, and are often used in smaller, confined spaces.
- Regular Inspections and Maintenance: Regular inspections are necessary to ensure all components of the fire suppression system are in good working order. This includes checking smoke and heat detectors, inspecting sprinkler heads and suppression agent storage containers, and testing alarm systems.
- Employee Training: All employees should be trained on how to respond in the event of a fire, including evacuation procedures, how to use handheld fire extinguishers, and how to shut down sensitive equipment safely.
It's important to note that fire suppression systems should be designed with the layout and requirements of the specific data center in mind. For example, a data center with higher ceilings may require different smoke detection systems than one with lower ceilings.
Also, local fire codes and regulations must be adhered to when designing and installing these systems. Non-compliance can not only lead to legal penalties, but also compromise the data center's insurance coverage.
In summary, a well-designed and maintained fire suppression system is crucial for safeguarding a data center and its valuable data assets. It provides a line of defense against one of the most destructive physical threats, ensuring the continuity of operations and the preservation of critical data.
Disaster Preparedness
Disaster preparedness is a critical aspect of securing a data center, as it ensures that the facility and its data remain protected in the event of natural or man-made disasters. These could include events like floods, earthquakes, hurricanes, power outages, fires, and even cyber-attacks. By implementing robust disaster preparedness strategies, data centers can minimize service disruptions and data losses, ensuring business continuity.

Here are some key elements to consider for disaster preparedness:
- Risk Assessment: The first step in disaster preparedness is identifying potential risks specific to your data center location and operations. This includes evaluating geographical risks like earthquakes or floods, infrastructure risks like power stability, and operational risks like potential equipment failures or cyber threats.
- Disaster Recovery Plan: Once the risks have been identified, a comprehensive disaster recovery plan (DRP) should be developed. The DRP should outline the procedures to be followed in the event of each identified disaster scenario. This includes data backup and restoration procedures, equipment repair or replacement plans, and alternate operation procedures.
- Data Backup and Redundancy: Regular data backups are a critical part of disaster preparedness. Data should be backed up frequently and stored in a secure off-site location. For maximum protection, many data centers employ redundancy strategies, storing multiple copies of data across different locations.
- Infrastructure Redundancy: Just like data, infrastructure redundancy is also important. This includes having backup power solutions like generators and uninterruptible power supply (UPS) systems, redundant network connections, and even redundant cooling systems.
- Physical Safeguards: Physical safeguards like seismic bracing for earthquake protection, flood barriers for flood-prone areas, and fire-resistant materials can help protect the data center infrastructure against natural disasters.
- Emergency Response Training: All staff should be trained on the disaster recovery plan and emergency response procedures. This includes evacuation drills, training on how to safely shut down systems, and awareness of their roles and responsibilities during a disaster.
- Regular Testing and Updates: Disaster recovery plans should be tested regularly to ensure their effectiveness and to identify any potential areas of improvement. It's also important to keep the plan updated to reflect any changes in the data center's operations, technology, or the surrounding environment.
- Insurance: Appropriate insurance coverage can provide a financial safety net in the event of a disaster. It's important to understand what your policy covers and to update it as necessary to reflect changes in the value of your data center's assets.
By incorporating these elements into a comprehensive disaster preparedness plan, data centers can ensure they are well-equipped to handle potential disaster scenarios. This not only protects valuable data assets but also contributes to the overall trust and reliability that clients place in the data center's operations.
Security Personnel
Security personnel play a pivotal role in data center physical security. While technologies like CCTV cameras, intrusion detection systems, and access control systems offer crucial support, human vigilance and response capabilities are still paramount. Skilled security personnel can assess situations, make judgement calls, and respond appropriately, often preventing incidents before they escalate.

Below are some key aspects to consider regarding the role of security personnel in data centers:
- Security Guard Presence: Having security guards physically present at the data center is a significant deterrent to potential intruders. They can monitor the site, conduct patrols, control access points, respond to incidents, and provide a quick reaction to any security alerts.
- Screening and Verification: Security personnel are responsible for verifying the identity of individuals seeking to access the facility. They ensure that only authorized individuals are allowed entry, using tools like badge reader systems, biometric scanners, or manual verification against access lists.
- Monitoring Surveillance Systems: CCTV cameras and other surveillance systems are most effective when actively monitored. Security personnel can monitor real-time footage, spot suspicious activities, and take immediate action as needed.
- Incident Response: In case of a security breach or incident, security personnel play a crucial role in the immediate response. This could include apprehending trespassers, contacting law enforcement, or coordinating with other staff to ensure the safety and integrity of the data center.
- Routine Security Checks: Regular security checks and patrols around the data center can identify potential security threats or weaknesses. This can include checking the perimeter fence, ensuring doors are properly secured, or checking for any unusual activity.
- Emergency Procedures: In case of emergencies like fires, natural disasters, or other crisis situations, security personnel are typically trained in emergency response procedures. They can help with evacuations, liaise with emergency services, and ensure that safety protocols are followed.
- Training and Skills: Security personnel should undergo regular training to keep their security knowledge and skills up to date. This can include training in first aid, fire safety, incident response, as well as updates on the latest security threats and technologies.
- Communication: Effective communication skills are essential for security personnel. They need to communicate with other staff members, visitors, law enforcement, and emergency services. They may also need to produce written reports on incidents or security breaches.
While security personnel add an important layer of security, they should not be the only line of defense. The most secure data centers utilize a balanced, multi-layered approach, combining technology, physical barriers, and security personnel. This approach ensures that even if one layer is compromised, other layers continue to provide protection.
Conclusion
In conclusion, physical security in data centers is of paramount importance. A well-implemented security strategy not only safeguards critical data and assets but also ensures the continuity of business operations and enhances the reputation of the facility in terms of trust and reliability.
This involves a comprehensive and layered approach, inspired by the structure of medieval castle fortification, ranging from the physical structure of the data center and perimeter protection to secure access control using technologies like badge readers. Surveillance systems, providing real-time monitoring and alert capabilities, along with robust fire suppression systems, are indispensable components for risk mitigation.
In addition, disaster preparedness through risk assessments, disaster recovery plans, data and infrastructure redundancy, physical safeguards, and regular testing and updates is vital to ensure resilience against natural and man-made disasters. The role of security personnel, equipped with the necessary skills and training, cannot be overstated, as they provide the much-needed human element in maintaining and enhancing the security posture of the facility.
However, it's essential to remember that a data center's physical security needs are not a one-size-fits-all. They should be continuously reviewed, evaluated, and adjusted in response to the unique needs of the facility, technological advancements, emerging threats, and evolving industry best practices.
By keeping these factors in mind and prioritizing physical security, data centers can protect their critical assets and continue to provide the high level of service that clients expect, maintaining their position as trusted custodians in our increasingly data-driven world.
